Anvil is releasing a white paper today describing a technique that we have found useful to bypass secure boot on a number of embedded Linux devices where the file systems have been split into a signed/protected partition for executables, and a non protection partition to store persistent data.
Secure boot is an integral part of a secure Linux-based embedded system which requires every stage of the boot process to be cryptographically verified. With a typical Linux embedded system, the root of trust starts in the CPU. A boot ROM located within the CPU starts the boot process, loads the bootloader from external flash, verifies its signature, and starts executing the bootloader if the signature is valid. Next, the bootloader loads the next stage, verifies the signature and so on:
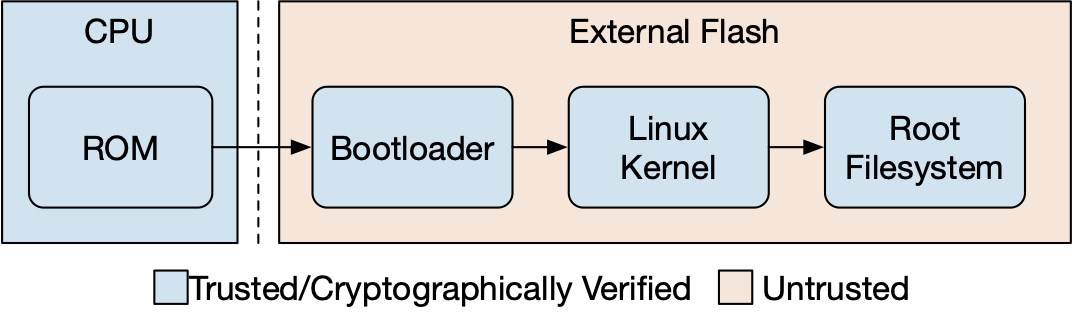
It is vital to include the root filesystem in the verification chain. However, this presents the embedded developer with a problem: since the root file system has been cryptographically signed, it can neither be changed nor used to store persistent data. Where then can an embedded developer store device-specific data such as configurations and logs between reboots? A common solution is to create an unprotected storage partition for non-volatile data (data that can be retrieved after power cycling) and mount it in a location such as /storage.
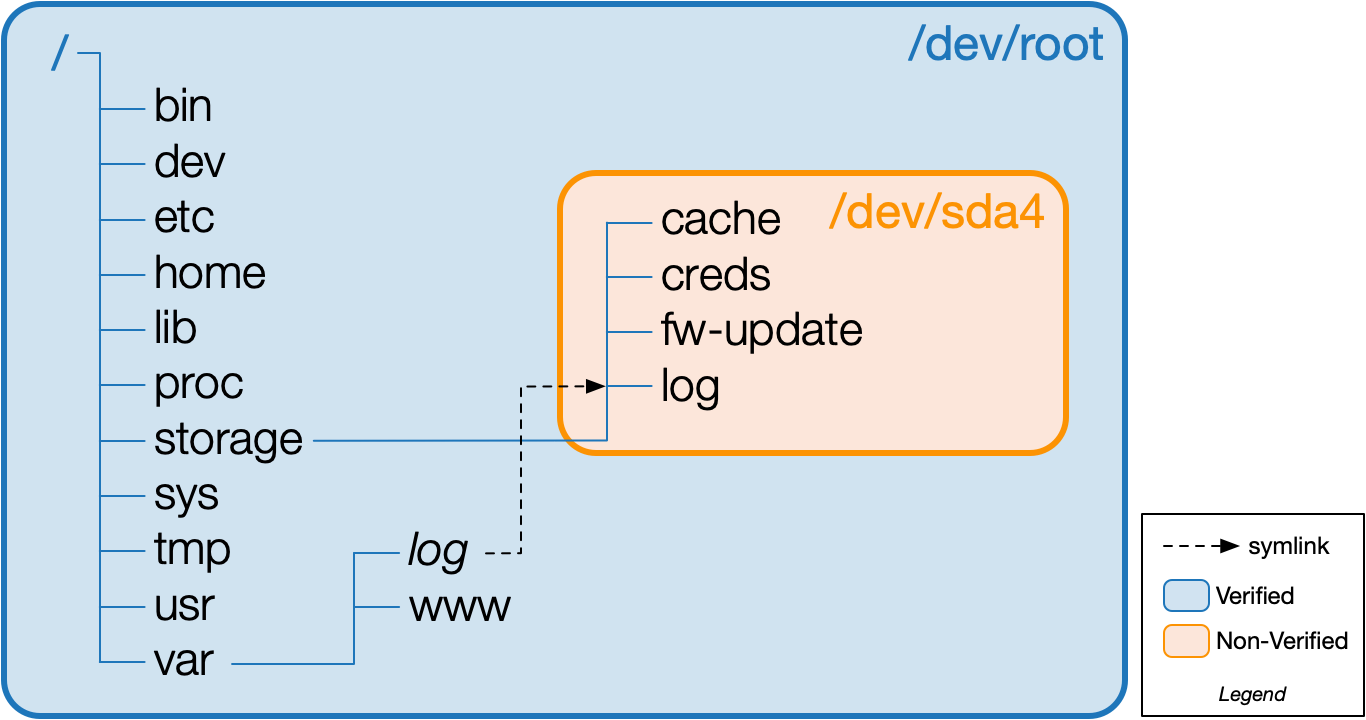
Ideally, the non-volatile storage partition should be protected with cryptographic integrity checks, but from our experience, this is rarely done.
The result is that the file system is split in two: a cryptographically-verified partition with executable binaries and a non-verified storage partition for data. While embedded developers may treat the data stored on the non-verified storage partition with suspicion, they frequently overlook the fact that the file system itself cannot be trusted. Trusting a non-verified file system creates an opportunity to leverage the file system to attack the embedded device.
The purpose of this white paper is to demonstrate the use of file system features of a non-verified partition such as symbolic links (symlinks) and to a lesser extent hard links to defeat secure boot protection. The use of symlinks to attack the secure boot of a Linux-based embedded device is rarely explored, and so is the focus of our research.
Our research demonstrates that having a non-verified partition can lead to comprise so the paper recommends extending cryptographic integrity protections to all partitions, but also includes recommendations on how to reduce some of the impacts when this is not possible.
The white paper can be viewed here: Defeating Secure Boot with Symlink & Hard Link Attacks
In addition, we are posting the virtual machine (https://github.com/anvilsecure/symlink-secure-boot-vm) used to simulate the scenarios described in the white paper and you can use the virtual machine to experiment and test out the attack scenarios.
About the Author
Michael Milvich is a Fellow at Anvil Secure. Prior to joining Anvil, Michael worked as a Senior Principal Consultant IOActive Inc, and as a Cyber Security Researcher at Idaho National Laboratory (INL). Michael got his start in embedded security hacking SCADA and ICS systems and later broadened to encompass a wide variety of embedded systems across many industries. Michael’s strong technical background combined with his years of general consulting have been utilized to assist some of the leading technologies and most advanced security groups in improving their security posture.